A vault is a tool for securely accessing secrets. A secret is anything that you want to tightly control access to, such as API keys, passwords, or certificates. Vault provides a unified interface to any secret while providing tight access control and recording a detailed audit log.
Vault Component
- Storage Backend: It configures the location for the storage of vault data.
- Secret Engines: It stores, generates, or encrypts data. Many secret engines can be enabled and used as needed. Secret engines are enabled and isolated at a “path”. All interactions are done directly with the path itself.
- Authentication methods: This component performs authentication to vault itself. This is responsible for assigning identity and policies to a user. Multiple authentication methods can be enabled depending on your use case. Once authenticated, Vault will issue a client token used to make subsequent vault requests(read/write).
- Audit devices: Keeps detailed logs of all requests and respond to the vault. Sensitive information is hashed before logging.
Install Vault
- Download vault from this link: Click here
- Unpackage vault to a directory
- Set the path to executable.
- Run the below command to check that vault is installed and the path is set.
Vault
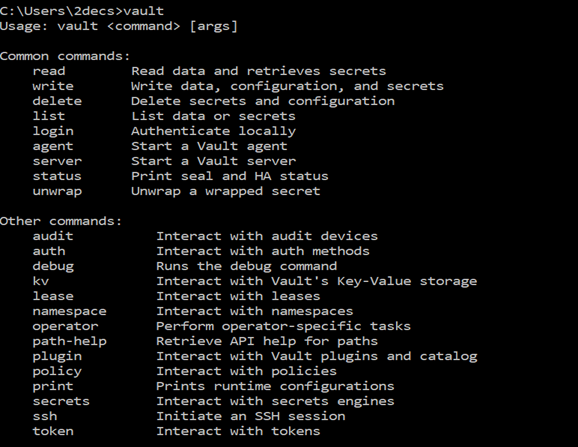
Starting the server
To start the vault server, Run the below command.
Vault server -dev
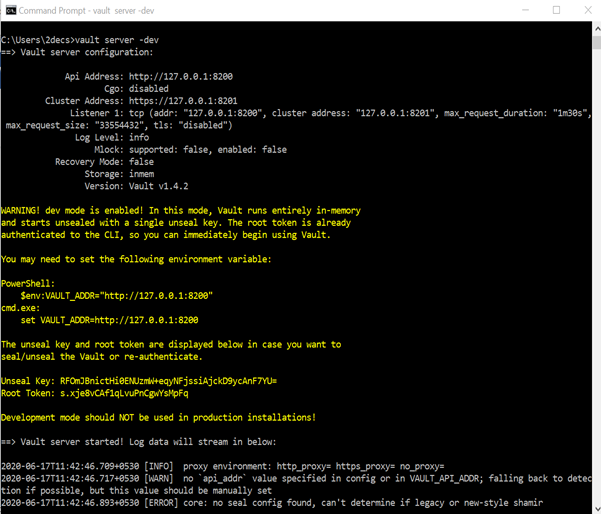
In this image, you will see that server is running on http://127.0.0.1:8200
And root token.
Accessing vault
Vault has three interfaces to interact with : UI, CLI and HTTP API.
Not all vault features are available via UI and CLI but all can be accessed via HTTP API.
Authentication required to access any of the interfaces.
Who uses what interfaces
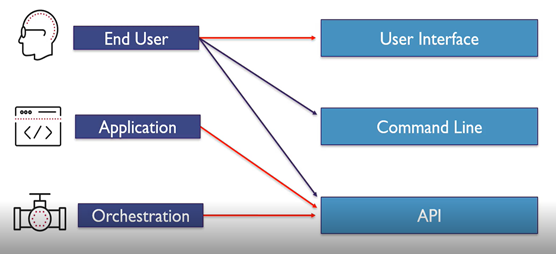
Accessing vault using UI
Access UI on port 8200
Runs on Same IP as Listener
Vault UI enables Access to configure:
- k/v store
- Authentication methods
- Secret engines
- Group and Entities
- Policies (ACLs)
- Direct access to CLI
- Replication (Enterprise)
- Licensing (Enterprise)
Open the Vault UI
- Open this URL in browser http://127.0.0.1:8200.
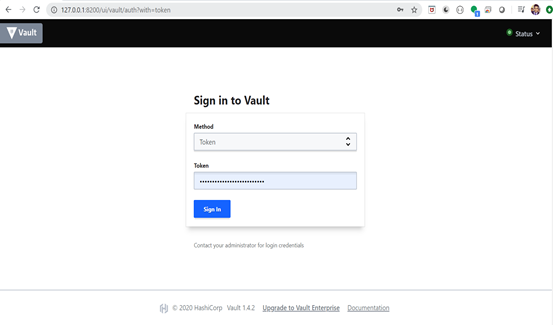
- Login with token and click on Enable new engine
- Select one secret engine and click on next button.
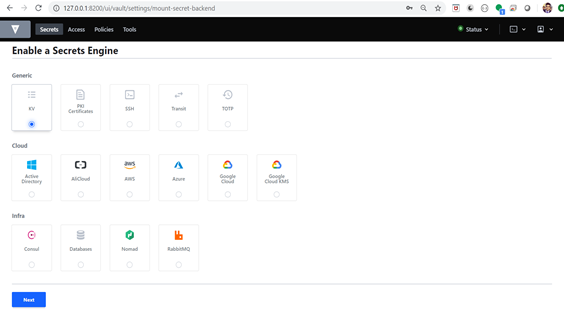
- Type the path and select the version. Click on enable engine
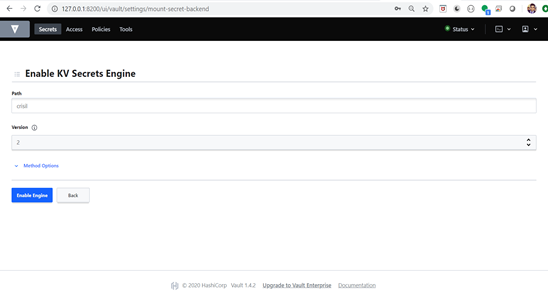
Now a secret engine is created.
- In the below image, You can see a newly created secret engine with the path.
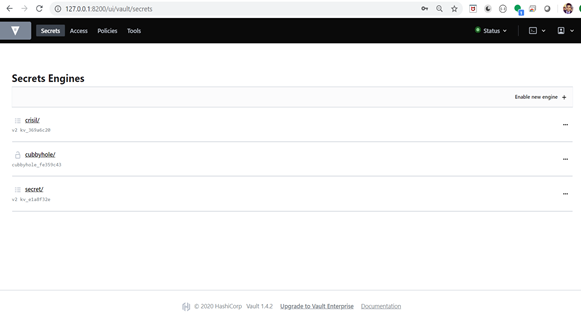
- Now click on crisil.
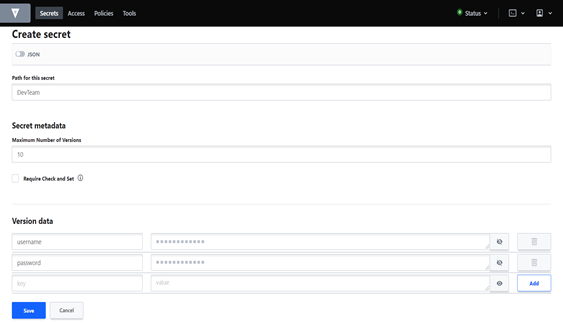
- Create the secret.
- Click on “create secret” and save the credential.
Create the policies
What are vault policies:
Provides a way to permit or deny access to certain paths or action within vault.
Provides authorization using a declarative policy written in HCL and JSON.
Permission includes:
- Create
- Read
- Update
- Delete
- List
- Deny
- Sudo
Using the * and +
- The glob(*) is a wildcard and can only be used at the end of a path.
- It can be used signify anything after a path or part of of a pattern.
– crisil/DevTeam/*
- The plus(+) denotes any numbers of characters within a single path segment (crisil/+/db – matches secret/DevTeam/db or secret/UATTeam/db)
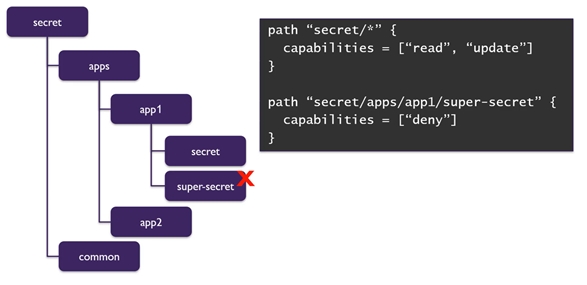
Using Deny:
If want to give permission of all the folder except few. In this case we can use deny.
Below image will be helpful to understand the scenario.
STEPS TO CRATE THE POLICY
- Click on the policies
- Click on create policies.
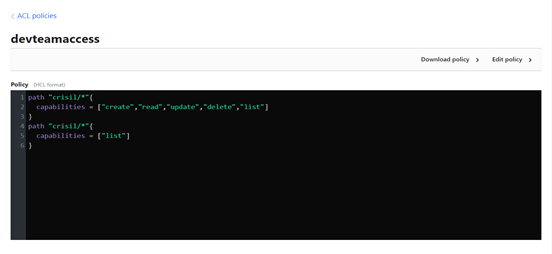
- You can directly upload the policy or write the policy and hit the save button.
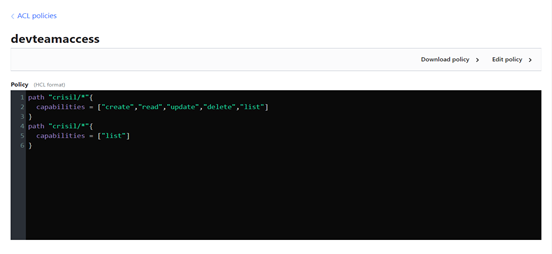
You can write policy as per your requirement.
Note: All the permission should be written in small letters
STEPS TO CREATE THE GROUPS:
Access-> Group -> Create Group
- Type the group name.
- Select the policy. Which you want to on this group.
- Hit the create button.
Now Group is created.
Now we need to add the group member in this group.
To do this, We need to create group member (Entity/Users).
Note: Before creating users, We required authentication methods.
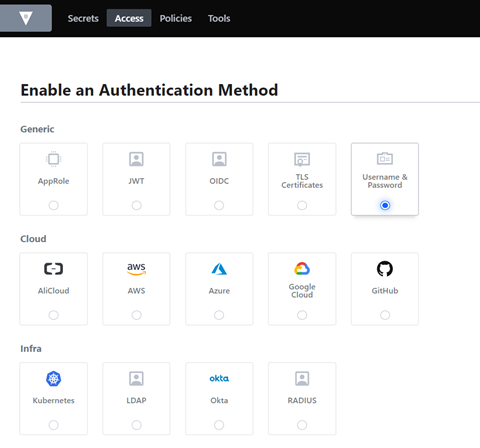
STEPS TO ENABLE AUTHENTICATION METHODS
Access -> Auth method -> Enable new method
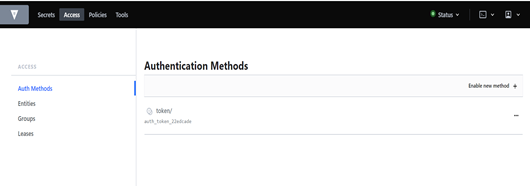
Now select any of the auth method.
For this demo I am selecting Username & password.
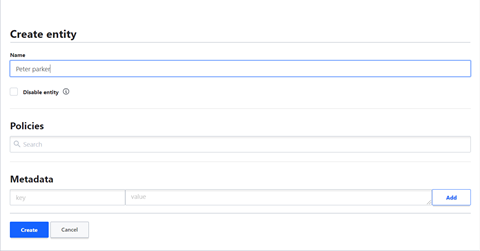
STEPS TO CREATE THE ENTITY
Access -> Entity -> Create Entity
Fill the name and hit the create button
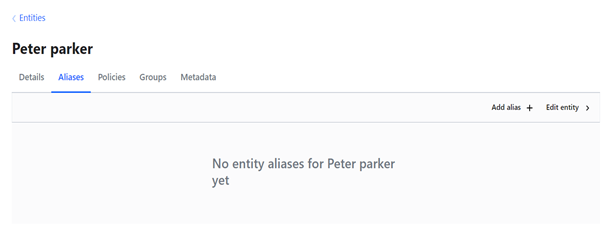
Now add the alias. (Alias is basically representation of user name).
Click on “Add alias” and fill the alias name and select the auth method.
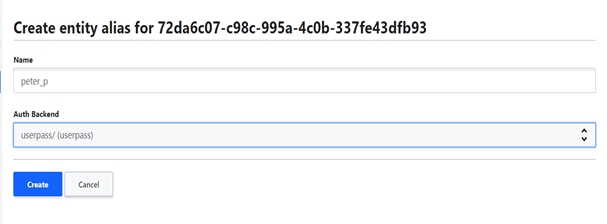
Leave the policy blank because we inheriting the policy from the group. Otherwise you can directly add the policy with the user.
Now Go back to group and edit it.
No add the member in this group as shown below.
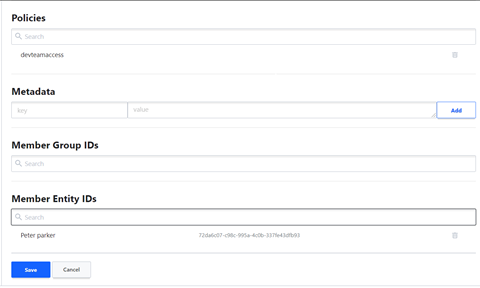
Now we have added User , group and policy.
But we haven’t added password.
UI doesn’t support to set the password. You will required CLI to set the password.
To create Password: open a new CLI and run these three commands.
- set VAULT_ADDR=http://localhost:8200/
- set VAULT_TOKEN=<Root token>
- vault write auth/userpass/users/<alias> password=<“password”>
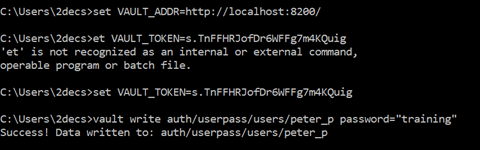
Each user has a token. To get token of user, Run the below command as shown in the image.
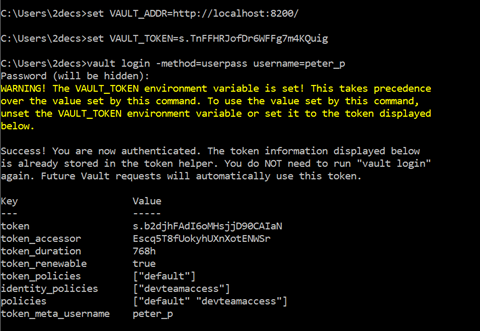
You can Directly login using
